We use Debian for our programs. Not solely as a result of we adore it, but additionally as a result of you possibly can harden and safe it very nicely. One of the numerous safety precausions for Debian-based Linux distributions are unattended upgrades.
Unattended upgrades will (clearly) improve your Debian-based system unattendenly. If we preserve it easy, that is principally an automatic apt-get improve with some tweaks. That’s it – that’s unattended upgrades!
Why ought to I exploit them?
Well, all of it is determined by your atmosphere and your patching behaviour and doubtless your (enterprise) processes. I had some discussions with buddies and clients of ours, and that is what I’ve heard up to now:
Pros for unattended upgrades
- You need your programs at all times to be up-to-date
- You need your programs at all times to have the newest safety patches
- You don’t need to patch them often by hand
- Even if you happen to miss the information of a brand new vulnerability, you need it to be patched
Cons for unattended upgrades
- You can’t do it, as a result of your enterprise firm says you solely have a number of particular patch home windows
- You know your utility breaks if you happen to replace it mechanically
- You need to do all the things by hand, or a minimum of invoke an automatic improve course of by hand, so that you’ve all the things below management
- You’ve a correct vulnerability administration and do safety upgrades primarily based on this
Never belief a human
I’m extra the let’s-do-it-unattended-guy, as a result of IMHO that is the a lot better possibility than the remaining. I’ve additionally my points with the explanations I’ve heard for the cons.
Let me begin with the (for my part) most evident downside in refusing unattended upgrades – the human being. We’re unhealthy in doing issues correctly 100% of the time. We’re people and that is a part of our nature – we’re not good and we make errors, that is how we be taught and evolve. But much more essential, we would have unhealthy days, we’re below stress, we’ve lots of work, we go on trip and we neglect issues. Now, what occurs if there’s a brand new vulnerability and also you’re simply missed or forgot it? What occurs if you happen to’re on trip, otherwise you’ve manner an excessive amount of work to even test into the newest vulnerability? It most likely received’t get patched (in time), and I feel all of us agree that that is actually unhealthy! So simply having religion in a human operator is a nasty choice 😉
Enterprise firms and their insurance policies
As talked about earlier than, enterprise firms are inclined to outline patch home windows, which principally means you possibly can solely improve a sure server / service in a particular time window. That isn’t very agile, is it? You want to grasp the motivation behind this administration choices. Lots of people, particularly in administration, are afraid of IT points, reminiscent of downtimes. Because of that, they’re afraid of modifications, they usually begin to refuse them. Never contact a working system, proper? 😉
But what if you should utilize that concern on your personal benefit? What if you happen to present them the draw back of this choice? What if you happen to use their concern in opposition to them? What if you happen to say them one thing like:
So we’ve possibility A, which implies we wait on your pretty patch window – which implies our programs are susceptible till that time – which implies we will get hacked – which implies that may hurt the corporate – which implies, after all, somebody’s chargeable for that little accident – which implies you may give it some thought if you’re going to sleep.
Then we’ve possibility B, which implies we do it mechanically – which implies our programs are at all times up-to-date – which implies they’re safe – which implies all people’s comfortable – which implies you possibly can fall asleep with a transparent conscience.
Just to be clear right here, IMHO possibility A (typically) is the retarded possibility and solely is smart in some exceptions. You ought to definitly goal for possibility B.
Exceptions
Of course, not each atmosphere is as black & white as described right here. I simply tried to maintain it a bit witty. Still, it is best to attempt to keep away from people and do it mechanically. Regardless of your choice, there may at all times be some exceptions. But that doesn’t imply you possibly can’t do unattended upgrades for almost all of servers, providers or packages.
Getting it up & prepared
Installation
Debian already has a pleasant documentation about unattended upgrades. The documentation is good and I used it to get it up & working. However, that is only for the fundamental setup and I had to determine the deets on my own.
So let’s begin by putting in the required packages:
apt-get set up unattended-upgrades apt-listchanges
- unattended-upgrades is doing the unattended upgrades (apparent, huh?)
- apt-listchanges reveals or mails the modifications of a bundle earlier than putting in it
Configuration
The configuration recordsdata in query are the next:
/and so on/apt/apt.conf.d/20auto-upgrades /and so on/apt/apt.conf.d/50unattended-upgrades /and so on/apt/listchanges.conf
First of all of the 20auto-upgrades file:
APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1";
This principally says do an apt-get replace and apt-get improve day-after-day, thus the quantity 1 (n-days) as worth.
Next up, the 50unattended-upgrades file:
Unattended-Upgrade::Origins-Pattern {
"origin=Debian,codename=${distro_codename},label=Debian-Security";
};
Unattended-Upgrade::Package-Blacklist {
};
Now, on this file you’ve the selection which packages ought to be upgraded. Debian already explains so much within the default configuration, which is:
// Lines beneath have the format format is "key phrase=worth,...". A
// bundle shall be upgraded provided that the values in its metadata match
// all of the equipped key phrases in a line. (In different phrases, omitted
// key phrases are wild playing cards.) The key phrases originate from the Release
// file, however a number of aliases are accepted. The accepted key phrases are:
// a,archive,suite (eg, "steady")
// c,part (eg, "major", "contrib", "non-free")
// l,label (eg, "Debian", "Debian-Security")
// o,origin (eg, "Debian", "Unofficial Multimedia Packages")
// n,codename (eg, "jessie", "jessie-updates")
// website (eg, "http.debian.internet")
// The accessible values on the system are printed by the command
// "apt-cache coverage", and could be debugged by working
// "unattended-upgrades -d" and searching on the log file.
//
// Within strains unattended-upgrades permits 2 macros whose values are
// derived from /and so on/debian_version:
// ${distro_id} Installed origin.
// ${distro_codename} Installed codename (eg, "jessie")
Last however not least, the listchanges.conf file:
[apt] frontend=pager verify=false email_address=root save_seen=/var/lib/apt/listchanges.db which=information
This is the file used to configure listchanges, which retains observe of modifications. Just be sure your mail config is working and the e-mail deal with is outlined accurately.
Running it
unattended-ugprades is working mechanically and is named by way of cronjob. You don’t want to put in apticron or alike, as talked about in a number of different posts.
If you need to debug it, you possibly can simply run it on the CLI by way of:
unattended-upgrades -d
Logging
If you need to know what was occurring, test the logfile positioned right here:
/var/log/unattended-upgrades/
You also can add the next configuration to ship you mails when an improve occured:
Unattended-Upgrade::Mail "root"; Unattended-Upgrade::MailOnlyOnError "false";
How we do it
Our configuration
For our infrastructure, we’re putting in and configuring unattended-upgrades mechanically by way of Ansible on each server. Here’s our default configuration with feedback.
20auto-upgrades:
// // !!! WARNING: This file is managed by Ansible, DON'T EDIT it manually !!! // // Enable unattended upgrades. APT::Periodic::Enable "1"; // Do "apt-get improve" each n-days (0=disable). APT::Periodic::Unattended-Upgrade "1"; // Do "apt-get improve --download-only" each n-days (0=disable). APT::Periodic::Update-Package-Lists "1"; // Do "apt-get improve --download-only" each n-days (0=disable). APT::Periodic::Download-Upgradeable-Packages "1"; // Do "apt-get autoclean" each n-days (0=disable). APT::Periodic::AutocleanInterval "7";
50unattended-upgrades:
//
// !!! WARNING: This file is managed by Ansible, DON'T EDIT it manually !!!
//
Unattended-Upgrade::Origins-Pattern {
"o=Debian,n=${distro_codename},l=Debian-Security";
};
Unattended-Upgrade::Package-Blacklist {
};
// Automatically run "dpkg --force-confold --configure -a".
Unattended-Upgrade::AutoFixInterruptedDpkg "true";
// Do computerized elimination of latest unused dependencies after the improve.
Unattended-Upgrade::Remove-Unused-Dependencies "true";
// Install upgrades when the machine is shuting down as an alternative of doing it within the background.
Unattended-Upgrade::InstallOnShutdown "false";
// Automatically reboot if the file /var/run/reboot-required is discovered after the improve.
Unattended-Upgrade::Automatic-Reboot "false";
// Automatically reboot even when there are customers at the moment logged in.
Unattended-Upgrade::Automatic-Reboot-WithUsers "true";
// If computerized reboot is enabled and wanted, reboot on the particular time.
Unattended-Upgrade::Automatic-Reboot-Time "now";
// Enable mail notifications.
Unattended-Upgrade::Mail "<our-own-mail>@verify.ch";
Unattended-Upgrade::MailOnlyOnError "true";
// Enable logging by way of syslog.
Unattended-Upgrade::SyslogEnable "true";
Unattended-Upgrade::SyslogFacility "daemon";
Security-related vs. non-security-related updates
As you possibly can see, we mechanically set up security-related updates day-after-day within the background. This ensures our programs get an important safety patches. For the replace of each different bundle, we use an Ansible playbook which merely does a dist-upgrade with a little bit of exception dealing with, adopted by working all configuration playbooks once more with a remaining reboot.
Monitor for reboots
We don’t mechanically reboot our programs, as a result of we don’t need them to go utterly down in the course of the day. Of course you possibly can schedule it by defining the reboot time (aside from now), however our method is a bit totally different.
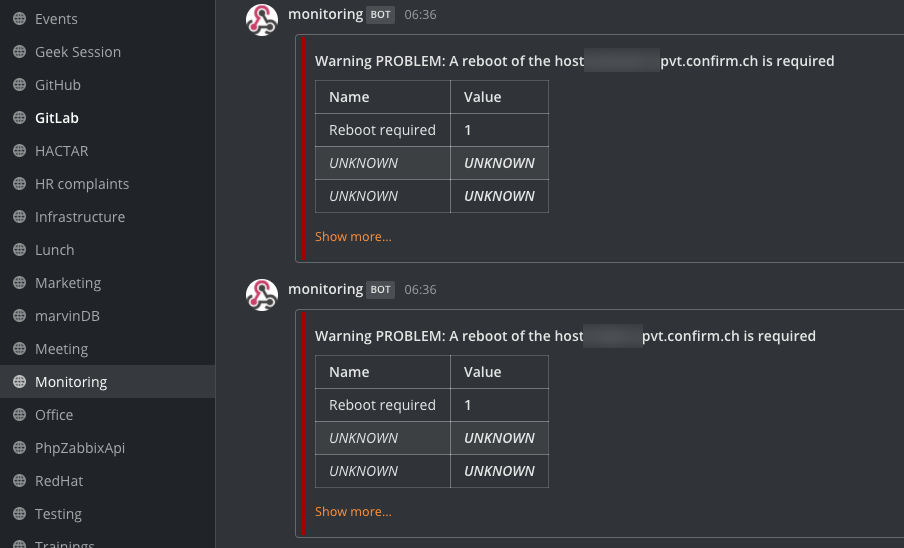
We merely monitor for the /var/run/reboot-required file in our monitoring and generate an alert in Zabbix:
This generates an alter to our Mattermost monitoring channel, so that everyone in our workforce is aware of concerning the “difficulty” and a reboot could be scheduled:
Verdict
Combining unattended safety upgrades with automated attended full system upgrades is IMHO a pleasant solution to preserve your atmosphere up-to-date and safe, with out dropping management of important upgrades the place a programs engineer is required.

