Last week I needed to strive the GitHub container registry in its place for Azure Container Registry. Since many issues are transferring in the direction of GitHub this appeared a good suggestion.
The plan I needed to execute was as follows:
* Build a Docker Container with GitHub Actions
* Push a Docker Container to the GitHub Container Registry
* Pull the Container Locally
* Pull the container on Azure Kubernetes Service (AKS)
So that is what I did, and the steps I adopted are documented under.
Build and Push a Docker Container with GitHub Actions
This was fairly simple. First I created this repository the place I created a quite simple Dockerfile (Based on this superior repo After that I added a GitHub motion workflow that builds and pushes this to the GitHub registry.
When navigating to the Actions tab on the repo, you’ll be able to choose the starter workflow “Publish Docker Container”, to get you began.
When you select to arrange this workflow, the very first thing it is advisable to do is change the IMAGE_NAME . After that you’re virtually performed, besides that it is advisable to take discover of the next part.
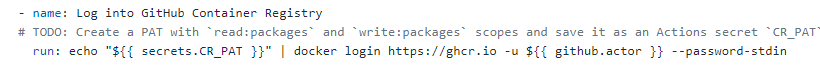
Because the GitHub Container Registry continues to be in Beta, you can’t use the usual Github Secrets but. To entry the GitHub Container Registry it is advisable to create a Personal Access Token with permissions to push and pull packages after which add this as a secret to your repository.
To create a Personal Access Token, navigate to your profile settings and create one within the Developer Settings part. Follow this information on Github Docs to create a PAT. Make certain you test the write:packages, learn:packages and delete:packages permission.

Once you created the PAT, be sure to put it aside in your clipboard. Navigate to your repository settings, and add a secret referred to as CR_PAT and add the PAT you saved on the clipboard.

Back in your GitHub Actions, now you can begin the Action to construct and push the container.
When your construct accomplished succesfully, you’ll be able to navigate to the packages part of your account, to see the Docker picture. E.g.

Pull the Container Locally
Great! We managed to push a container to Github Container Registry. Now we have to use the picture. Locally it really works fairly easy. You must login to the Github Container Registry with the identical PAT as you created within the Github Secrets. Then execute the command under and you’re good to go.
echo <YOUR_PAT> | docker login ghcr.io -u USERNAME --password-stdin
docker pull ghcr.io/<your_repository>/<your_imagename>
Look at this hyperlink for extra particulars on this
Configure AKS to make use of GitHub Container Registry
Azure Kubernetes Service (AKS) works with all Container Registries that observe the Docker registry interface. So, it additionally work with Github. Assuming that you have already got a AKS working, it is advisable to add a Pull Secret for the Github Container Registry.
From the command line you’ll be able to execute the next command
kubectl create secret docker-registry pullsecret --docker-server=With that you just add a secret to the AKS cluster. In your deployment, it is advisable to check with this pullsecret to get the containers. Look on the instance killerapp.deploy.yml and killerapp.service.yml recordsdata in my Git repository.
When you run kubectl apply -f killerapp-deploy.yml the pod can be deployed pulling the picture from the Github Container Registry!
Hope this helps!

